In the open source world everything lives/evolves/changes. This is why the new version of connecting latest FreeBSD 14.0-STABLE system to the FreeIPA/IDM is needed. One of the things that changed is that security/sssd is now deprecated and security/sssd2 is its successor. Also new version of ports-mgmt/poudriere-devel is available – with needed fixes already merged – and also with new restyled web interface.

I already messed with that topic several times in the past:
- Connect FreeBSD to FreeIPA/IDM
- Connect FreeBSD 13.2 to FreeIPA/IDM
- FreeBSD on FreeIPA/IDM with Poudriere Repo
This article will try to address and contain all steps needed – including setting up the FreeIPA/IDM server and including the Poudriere setup. Below You will find Table of Contents for this article. All of these systems will be Bhyve virtual machines.
- FreeIPA/IDM Server – Installation
- FreeIPA/IDM Server – Configuration
- Poudriere Server – Setup
- Poudriere Server – Build FreeIPA/IDM Client Packages
- Poudriere Server – Update Repo/Packages
- FreeBSD 14.0-STABLE Client – Setup
- FreeBSD 14.0-STABLE Client – Debug Commands
- Summary
The FreeBSD project recently started to provide ZFS based VM images … but unfortunately only for 14.0-RELEASE and they are not created for 14.0-STABLE or 15-CURRENT versions – so we will use the UFS based ones for both Poudriere server and FreeBSD FreeIPA/IDM client. For the record – https://download.freebsd.org/snapshots/VM-IMAGES/14.0-STABLE/amd64/Latest/ – they are available here.
Some note about commands run in this article – different colors for various hosts.
host # top -ba -o res 3 // executed on the host system [root@idm ~]# yum update -y // executed on IDM server root@freebsd:~ # geom disk list // executed on Poudriere server root@poudriere-devel-14-stable:~ # poudriere ports -l // executed on Poudriere server root@idm-client:~ # hostname idm-client.lab.org // executed on IDM client (FreeBSD) important information // marked as GREEN color
For the FreeIPA/IDM server I have used Alma Linux RHEL clone – but we know that Rocky Linux or Oracle Linux would also work well. We will use three systems in this article.
FreeIPA/IDM server – with idm.lab.org hostname.
OS: Alma Linux
IP: 10.0.0.200/24
GW: 10.0.0.1
domain: lab.org
realm: LAB.ORG
hostname: idm.lab.org
Poudriere builder system – with poudriere-devel-14-stable.lab.org hostname.
OS: FreeBSD 14.0-STABLE
IP: 10.0.0.124/24
GW: 10.0.0.1
DNS: 1.1.1.1
domain: -
realm: -
hostname: poudriere-devel-14-stable.lab.org
FreeBSD client for FreeIPA/IDM system – with idm-client.lab.org hostname.
OS: FreeBSD 14.0-STABLE
IP: 10.0.0.233/24
GW: 10.0.0.1
DNS: 10.0.0.200
domain: lab.org
realm: LAB.ORG
hostname: idm-client.lab.org
I really like the FreeBSD Bhyve memory ballooning – which means the guest VMs only take as much RAM as guest OS allocated and not 12 GB RAM as is configured.
host # vm list | grep -e STATE -e Running NAME DATASTORE LOADER CPU MEMORY VNC AUTO STATE idm default uefi 2 4g 0.0.0.0:5900 No Running (25284) idm-client-14-stable default bhyveload 2 1g - No Running (29517) poudriere-devel-14-stable default bhyveload 8 12g - Yes [1] Running (23419) host # top -ba -o res 3 last pid: 1290; load averages: 0.09, 0.09, 0.08 up 0+00:47:08 07:05:20 32 processes: 1 running, 31 sleeping CPU: 0.0% user, 0.0% nice, 0.6% system, 0.0% interrupt, 99.4% idle Mem: 2983M Active, 463M Inact, 1060M Wired, 56K Buf, 27G Free ARC: 619M Total, 115M MFU, 497M MRU, 32K Anon, 2346K Header, 4231K Other 551M Compressed, 1080M Uncompressed, 1.96:1 Ratio Swap: 4096M Total, 4096M Free PID USERNAME THR PRI NICE SIZE RES STATE C TIME WCPU COMMAND 25284 root 13 20 0 4159M 1168M kqread 13 3:12 1.27% bhyve: idm (bhyve) 23419 root 19 20 0 12G 109M kqread 15 0:27 0.00% bhyve: poudriere-devel-14-stable (bhyve) 29517 root 13 20 0 1075M 77M kqread 5 0:20 0.00% bhyve: idm-client-14-stable (bhyve)
As you can see I am using sysutils/vm-bhyve-devel for the Bhyve management – but You may as well use bare /usr/share/examples/bhyve/vmrun.sh instead … or even entirely different hypervisor like KVM on Linux or VirtualBox on Windows – it does not matter as long as machines have access to the Internet and they see each other in the same LAN network.
FreeIPA/IDM Server – Installation
I installed the Alma Linux some time ago – so the screenshot shows older 8.7 version.
After reboot its network is configured as shown below.
[root@idm ~]# cat /etc/sysconfig/network-scripts/ifcfg-enp0s3
TYPE=Ethernet
PROXY_METHOD=none
BROWSER_ONLY=no
BOOTPROTO=none
DEFROUTE=yes
IPV4_FAILURE_FATAL=no
IPV6INIT=no
IPV6_DEFROUTE=yes
IPV6_FAILURE_FATAL=no
IPV6_ADDR_GEN_MODE=eui64
NAME=enp0s3
UUID=120efe1f-3cb6-40cf-8aad-b17066c08543
DEVICE=enp0s3
ONBOOT=yes
IPADDR=10.0.0.200
PREFIX=24
GATEWAY=10.0.0.1
DNS1=1.1.1.1
IPV6_DISABLED=yes
Some more basic setup commands below.
[root@idm ~]# echo 10.0.0.200 idm.lab.org idm >> /etc/hosts [root@idm ~]# cat << EOF >> /etc/sysctl.conf # DISABLE IPv6 FOR MAIN enp0s3 INTERFACE net.ipv6.conf.enp0s3.disable_ipv6=1 EOF [root@idm ~]# hostnamectl set-hostname idm.lab.org [root@idm ~]# timedatectl set-timezone Europe/Warsaw [root@idm ~]# timedatectl set-local-rtc 0 [root@idm ~]# yum update -y [root@idm ~]# reboot
Continuation after reboot.
[root@idm ~]# yum module enable idm:DL1 -y [root@idm ~]# yum distro-sync -y [root@idm ~]# yum install -y bind-utils chrony nc [root@idm ~]# ipa-server-install \ --domain lab.org \ --realm LAB.ORG \ --reverse-zone=0.0.10.in-addr.arpa. \ --allow-zone-overlap \ --no-forwarders \ --ntp-pool pool.ntp.org \ --setup-dns \ --ds-password password \ --admin-password password \ --unattended [root@idm ~]# ipactl status Directory Service: RUNNING krb5kdc Service: RUNNING kadmin Service: RUNNING named Service: RUNNING httpd Service: RUNNING ipa-custodia Service: RUNNING pki-tomcatd Service: RUNNING ipa-otpd Service: RUNNING ipa-dnskeysyncd Service: RUNNING ipa: INFO: The ipactl command was successful [root@idm ~]# systemctl list-unit-files | grep ipa | grep service ipa-ccache-sweep.service static ipa-custodia.service disabled ipa-dnskeysyncd.service disabled ipa-healthcheck.service disabled ipa-ods-exporter.service disabled ipa-otpd@.service static ipa.service enabled [root@idm ~]# systemctl enable --now httpd [root@idm ~]# systemctl list-unit-files | grep httpd.service httpd.service enabled [root@idm ~]# systemctl disable firewalld [root@idm ~]# systemctl stop firewalld [root@idm ~]# cat /etc/sssd/sssd.conf [domain/lab.org] ipa_server_mode = True ipa_server = idm.lab.org ipa_hostname = idm.lab.org ipa_domain = lab.org id_provider = ipa auth_provider = ipa chpass_provider = ipa access_provider = ipa cache_credentials = True ldap_tls_cacert = /etc/ipa/ca.crt krb5_store_password_if_offline = True [sssd] services = nss, pam, ifp, ssh, sudo domains = lab.org [nss] homedir_substring = /home memcache_timeout = 600 [pam] [sudo] [autofs] [ssh] [pac] [ifp] allowed_uids = ipaapi, root [session_recording]
If you would like to see what a successful ipa-server-install(8) looks like – you can take a look HERE.
We have our FreeIPA/IDM server installed.
You will need to add 10.0.0.200 as idm.lab.org to your /etc/hosts on the system where you will be using the browser (or to your local DNS).
host # grep idm /etc/hosts
10.0.0.200 idm.lab.org idm
You can login to it typing https://10.0.0.200 at your local browser – you will be redirected to https://idm.lab.org/ipa/ui/ immediately and you will see the login page as shown below.
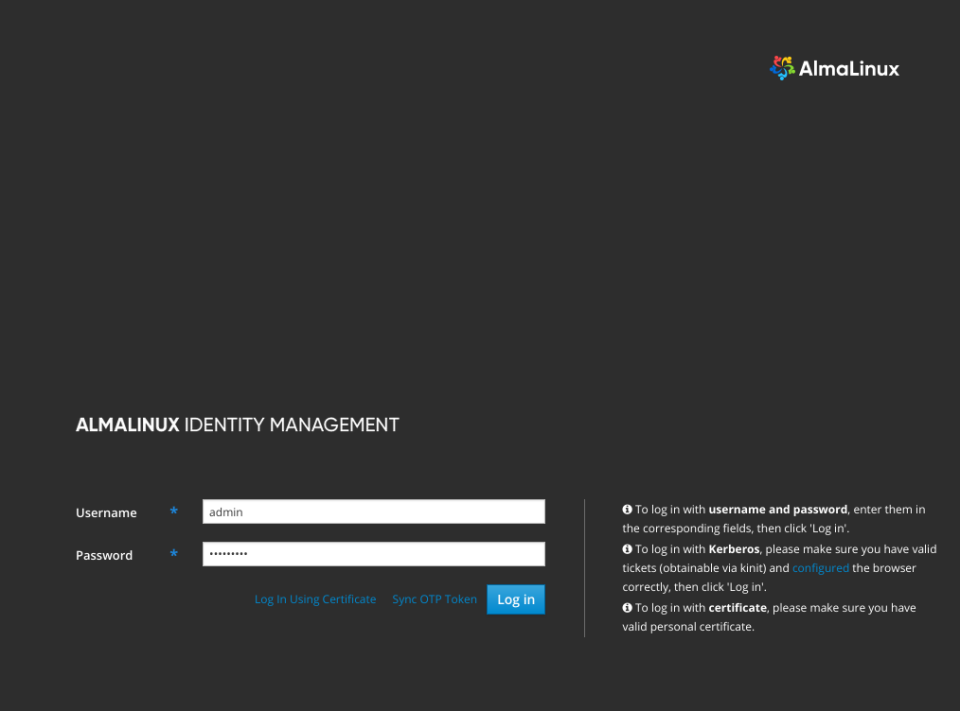
You may login with admin username and the password you specified for the ipa-server-install(8) command (or password if you just copy pasted that command 🙂
FreeIPA/IDM Server – Configuration
… and after logging in I created a regular vermaden user as shown below.
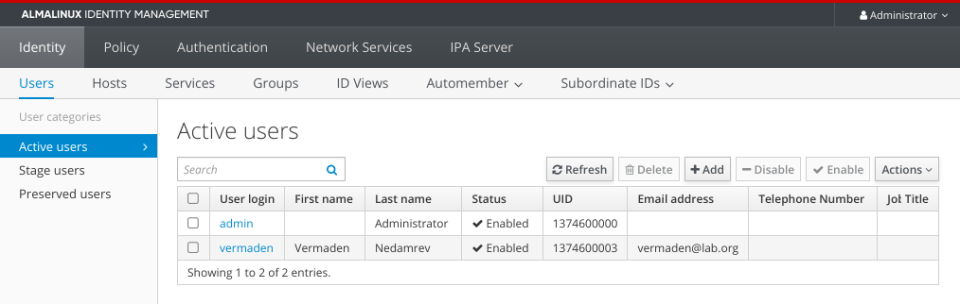
Keep in mind to reset your password by connecting to FreeIPA/IDM server.
host # ssh -l vermaden 10.0.0.200 (vermaden@10.0.0.200) Password: (vermaden@10.0.0.200) Password expired. Change your password now. Current Password: (vermaden@10.0.0.200) New password: (vermaden@10.0.0.200) Retype new password: Last failed login: Wed Oct 19 00:47:57 CEST 2022 from 10.0.0.33 on ssh:notty There was 1 failed login attempt since the last successful login. [vermaden@idm /]$ w 12:58:50 up 6:39, 1 user, load average: 0.02, 0.05, 0.00 USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT vermaden pts/0 10.0.0.4 12:58 1.00s 0.04s 0.01s w
The more important configuration is in HBAC and Sudo rules.
Here are HBAC related settings.
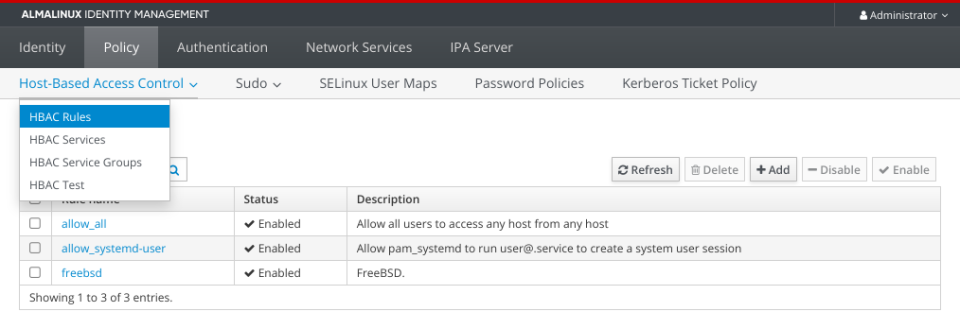
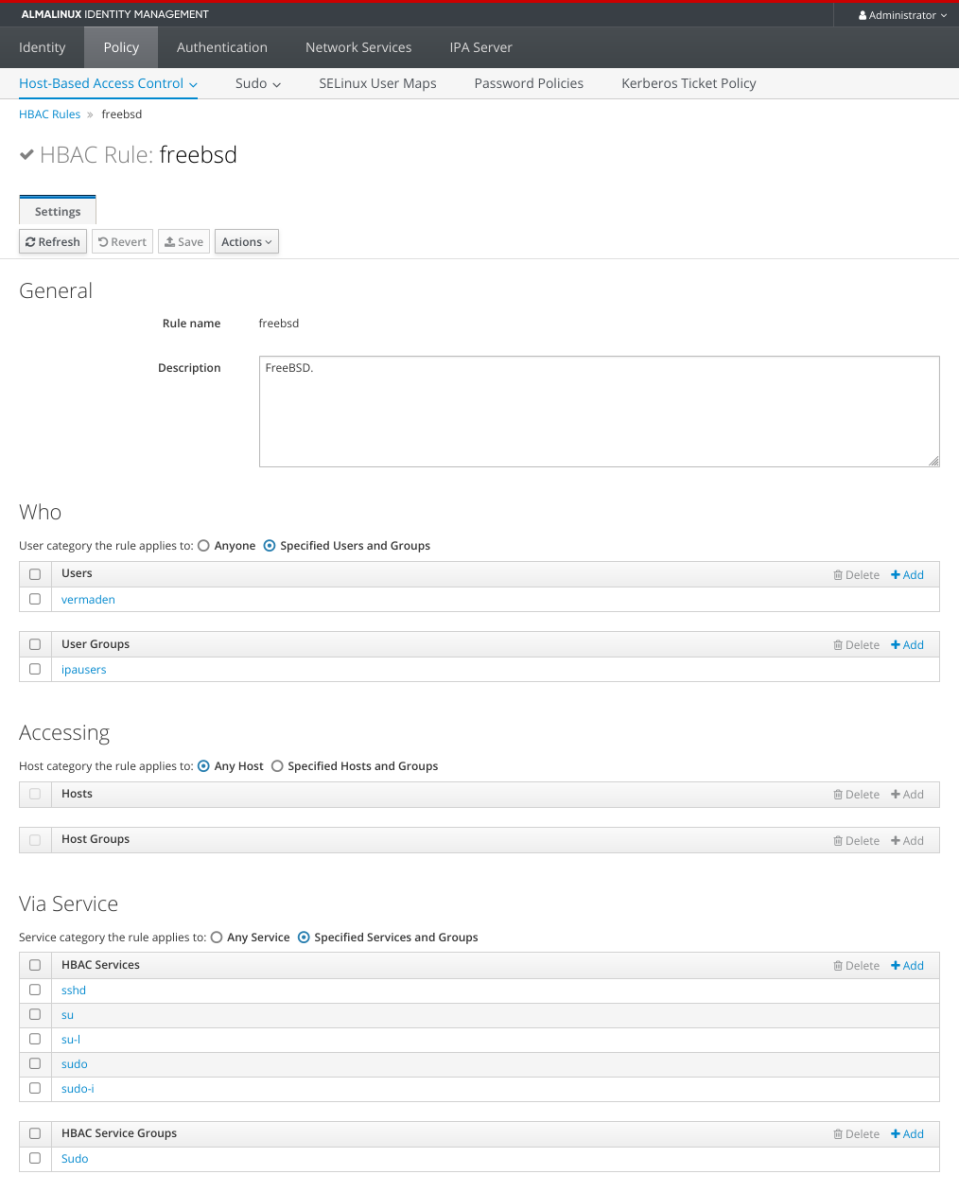
… and the Sudo part.
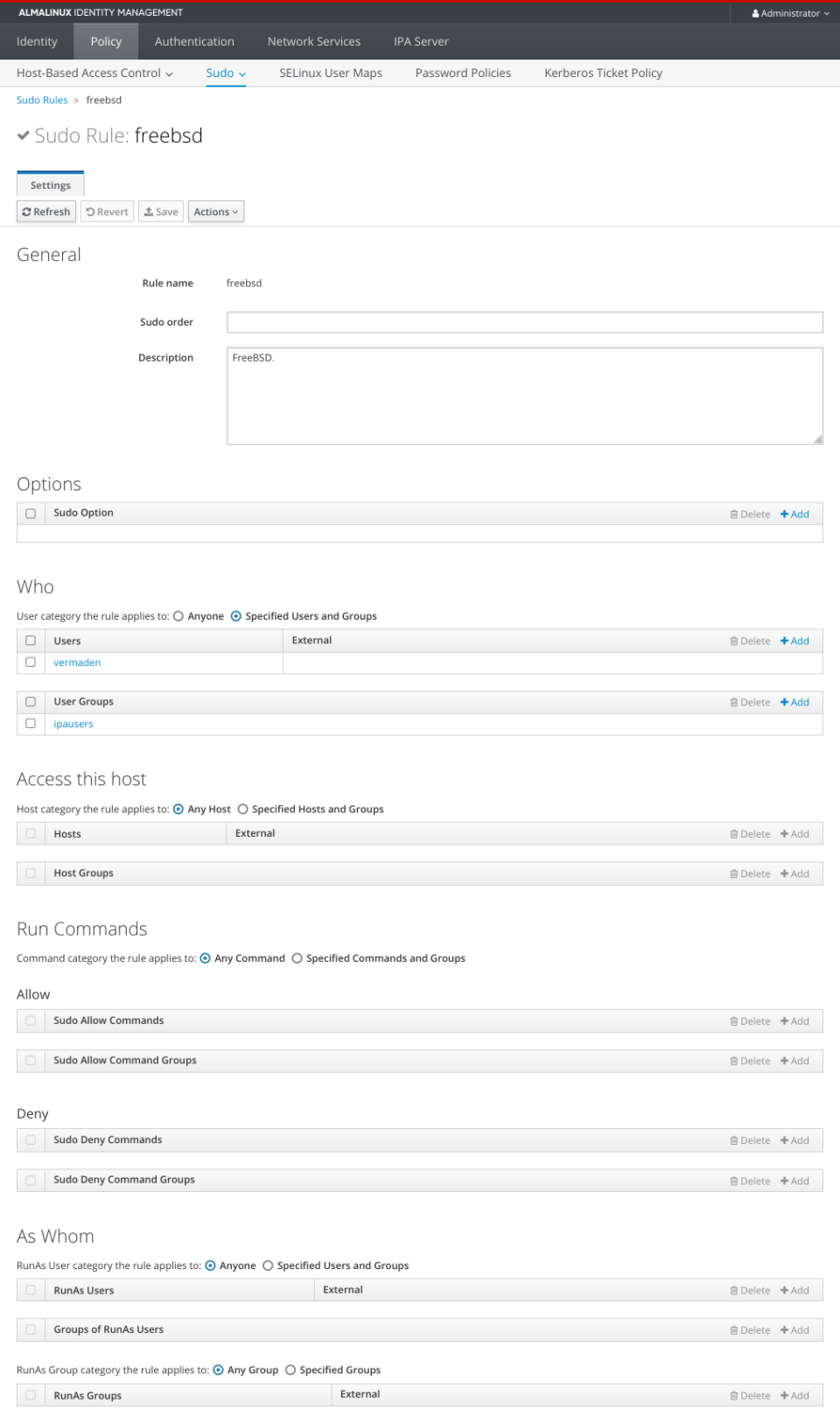
Poudriere Server – Setup
One note for the FreeBSD setups below – please use /bin/sh shell (default for root since 14.0-RELEASE) for the commands … or zsh(1) for example … or other POSIX compatible shell. Some of these commands may not work properly on ‘C’ based shells or in fish(1) shell.
This is the template I used for Bhyve VMs.
host # cat /vm/.templates/freebsd.conf
loader="bhyveload"
cpu=1
memory=256M
network0_type="virtio-net"
network0_switch="public"
disk0_type="nvme"
disk0_name="disk0.img"
We will now create poudriere-devel-14-stable VM for Poudriere server.
host # vm create -t freebsd -s 20g -m 12g -c 8 poudriere-devel-14-stable host # du -sgA /vm/poudriere-devel-14-stable/* 20 /vm/poudriere-devel-14-stable/disk0.img 1 /vm/poudriere-devel-14-stable/poudriere-devel-14-stable.conf 1 /vm/poudriere-devel-14-stable/vm-bhyve.log
Now we will replace disk0.img with Latest FreeBSD 14.0-STABLE snapshot.
host # fetch -o - 'https://download.freebsd.org/snapshots/VM-IMAGES/14.0-STABLE/amd64/Latest/FreeBSD-14.0-STABLE-amd64.raw.xz' \ | xz -d > /vm/poudriere-devel-14-stable/disk0.img host # file -b /vm/poudriere-devel-14-stable/disk0.img DOS/MBR boot sector; partition 1 : ID=0xee, start-CHS (0x0,0,2), end-CHS (0x3ff,255,63), startsector 1, 12649684 sectors host # du -sgA /vm/poudriere-devel-14-stable/* 7 /vm/poudriere-devel-14-stable/disk0.img 1 /vm/poudriere-devel-14-stable/poudriere-devel-14-stable.conf 1 /vm/poudriere-devel-14-stable/vm-bhyve.log
We now need to add additional disk1.img disk to for ZFS pool.
host # truncate -s 10G /vm/poudriere-devel-14-stable/disk0.img host # vm add -d disk -t file -s 100g poudriere-devel-14-stable host # vm info poudriere-devel-14-stable | grep -A 16 virtual-disk virtual-disk number: 0 device-type: file emulation: nvme options: - system-path: /vm/poudriere-devel-14-stable/disk0.img bytes-size: 10737418240 (10.000G) bytes-used: 1720046592 (1.601G) virtual-disk number: 1 device-type: file emulation: nvme options: - system-path: /vm/poudriere-devel-14-stable/disk1.img bytes-size: 107374182400 (100.000G) bytes-used: 1024 (1.000K) host # du -sgA /vm/poudriere-devel-14-stable/* 10 /vm/poudriere-devel-14-stable/disk0.img 100 /vm/poudriere-devel-14-stable/disk1.img 1 /vm/poudriere-devel-14-stable/poudriere-devel-14-stable.conf 1 /vm/poudriere-devel-14-stable/vm-bhyve.log
Now internally inside VM.
host # vm start poudriere-devel-14-stable Starting poudriere-devel-14-stable * found guest in /vm/poudriere-devel-14-stable * booting... host # vm console poudriere-devel-14-stable (...) Starting devd. Starting dhclient. DHCPDISCOVER on vtnet0 to 255.255.255.255 port 67 interval 4 DHCPOFFER from 10.0.0.1 DHCPREQUEST on vtnet0 to 255.255.255.255 port 67 DHCPACK from 10.0.0.1 bound to 10.0.0.23 -- renewal in 43200 seconds. add host 127.0.0.1: gateway lo0 fib 0: route already in table add host ::1: gateway lo0 fib 0: route already in table add net fe80::: gateway ::1 add net ff02::: gateway ::1 add net ::ffff:0.0.0.0: gateway ::1 add net ::0.0.0.0: gateway ::1 Updating motd:. Updating /var/run/os-release done. Clearing /tmp (X related). Creating and/or trimming log files. Starting syslogd. Mounting late filesystems:. Starting cron. Starting background file system checks in 60 seconds. Wed Mar 6 08:23:03 UTC 2024 FreeBSD/amd64 (freebsd) (ttyu0) login:
Use the root user with ’empty’ password – just hit [ENTER] key on password prompt.
root@freebsd:~ # :> ~/.hushlogin root@freebsd:~ # passwd root Changing local password for root New Password: Retype New Password: root@freebsd:~ # geom disk list Geom name: nda0 Providers: 1. Name: nda0 Mediasize: 10737418240 (10G) Sectorsize: 512 Mode: r3w3e8 descr: bhyve-NVMe lunid: 589cfc2012350001 ident: NVME-4-0 rotationrate: 0 fwsectors: 0 fwheads: 0 Geom name: nda1 Providers: 1. Name: nda1 Mediasize: 107374182400 (100G) Sectorsize: 512 Mode: r0w0e0 descr: bhyve-NVMe lunid: 589cfc20d2f40001 ident: NVME-4-1 rotationrate: 0 fwsectors: 0 fwheads: 0 root@freebsd:~ # zpool create zroot nda1 ZFS filesystem version: 5 ZFS storage pool version: features support (5000) root@freebsd:~ # zfs set mountpoint=none zroot root@freebsd:~ # zfs list NAME USED AVAIL REFER MOUNTPOINT zroot 100K 96.4G 24K none
Now some basic configuration.
root@freebsd:~ # cat /etc/rc.conf hostname="poudriere-devel-14-stable.lab.org" ifconfig_DEFAULT="inet 10.0.0.124/24 up" defaultrouter="10.0.0.1" zfs_enable="YES" sshd_enable="YES" nginx_enable="YES" root@freebsd:~ # cat /etc/hosts ::1 localhost localhost.my.domain 127.0.0.1 localhost localhost.my.domain 10.0.0.124 poudriere-devel-14-stable.lab.org poudriere-devel-14-stable root@freebsd:~ # service sshd start root@freebsd:~ # mkdir -p /usr/local/etc/pkg/repos root@freebsd:~ # sed -e s/quarterly/latest/g /etc/pkg/FreeBSD.conf \ > /usr/local/etc/pkg/repos/FreeBSD.conf root@freebsd:~ # pkg install -y \ beadm \ lsblk \ poudriere-devel \ nginx \ git-lite \ ccache4 \ tree root@freebsd:~ # reboot
Fortunately we do not need to patch ports-mgmt/poudriere-devel anymore as the -u flag for sort(1) is already there.
root@poudriere-devel-14-stable:~ # grep remote_all_ /usr/local/share/poudriere/common.sh | grep sort "${remote_all_options}" | sort -k1.2 -u | paste -s -d ' ' -) "${remote_all_dept}" | sort -u | paste -s -d ' ' -)
We will now setup actual Poudriere server.
root@poudriere-devel-14-stable:~ # export SSL=/usr/local/etc/ssl root@poudriere-devel-14-stable:~ # mkdir -p \ /usr/ports/distfiles \ ${SSL}/keys \ ${SSL}/certs root@poudriere-devel-14-stable:~ # chmod 0600 ${SSL}/keys root@poudriere-devel-14-stable:~ # openssl genrsa -out ${SSL}/keys/poudriere.key 4096 root@poudriere-devel-14-stable:~ # openssl rsa \ -in ${SSL}/keys/poudriere.key -pubout \ -out ${SSL}/certs/poudriere.cert root@poudriere-devel-14-stable:~ # zfs create -p -o mountpoint=/var/ccache zroot/var/ccache root@poudriere-devel-14-stable:~ # zfs list NAME USED AVAIL REFER MOUNTPOINT zroot 213K 96.4G 24K none zroot/var 48K 96.4G 24K none zroot/var/ccache 24K 96.4G 24K /var/ccache root@poudriere-devel-14-stable:~ # export IP=10.0.0.124 root@poudriere-devel-14-stable:~ # cat << EOF > /usr/local/etc/poudriere.conf ZPOOL=zroot BASEFS=/usr/local/poudriere ZROOTFS=/usr/local/poudriere FREEBSD_HOST=ftp://ftp.freebsd.org POUDRIERE_DATA=/usr/local/poudriere/data CHECK_CHANGED_OPTIONS=verbose CHECK_CHANGED_DEPS=yes PKG_REPO_SIGNING_KEY=/usr/local/etc/ssl/keys/poudriere.key URL_BASE=http://${IP}/ USE_TMPFS=no TMPFS_LIMIT=12 MAX_MEMORY=12 PARALLEL_JOBS=8 PREPARE_PARALLEL_JOBS=8 MAX_FILES=4096 DISTFILES_CACHE=/usr/ports/distfiles KEEP_OLD_PACKAGES=yes KEEP_OLD_PACKAGES_COUNT=3 CHECK_CHANGED_OPTIONS=verbose CHECK_CHANGED_DEPS=yes CCACHE_DIR=/var/ccache RESTRICT_NETWORKING=no EOF root@poudriere-devel-14-stable:~ # mkdir -p /usr/local/poudriere/data/logs/bulk root@poudriere-devel-14-stable:~ # ln -s \ /usr/local/etc/ssl/certs/poudriere.cert \ /usr/local/poudriere/data/logs/bulk/poudriere.cert root@poudriere-devel-14-stable:~ # service nginx enable root@poudriere-devel-14-stable:~ # sed -i '' -E 's|text/plain[\t\ ]*txt|text/plain txt log|g' /usr/local/etc/nginx/mime.types root@poudriere-devel-14-stable:~ # export IP=10.0.0.124 root@poudriere-devel-14-stable:~ # cat << EOF > /usr/local/etc/nginx/nginx.conf events { worker_connections 1024; } http { include mime.types; default_type application/octet-stream; server { listen 80 default; server_name ${IP}; root /usr/local/share/poudriere/html; location /data { alias /usr/local/poudriere/data/logs/bulk; autoindex on; } location /packages { root /usr/local/poudriere/data; autoindex on; } } } EOF root@poudriere-devel-14-stable:~ # service nginx restart root@poudriere-devel-14-stable:~ # mkdir -p /root/.cache/ccache root@poudriere-devel-14-stable:~ # ln -sf /var/ccache /root/.cache/ccache root@poudriere-devel-14-stable:~ # cat << EOF > /usr/local/etc/poudriere.d/make.conf ALLOW_UNSUPPORTED_SYSTEM=yes DISABLE_LICENSES=yes EOF root@poudriere-devel-14-stable:~ # cat << EOF > /var/ccache/ccache.conf max_size = 0 cache_dir = /var/ccache base_dir = /var/ccache hash_dir = false EOF root@poudriere-devel-14-stable:~ # poudriere jail -c -j 14-0-S-amd64 -v 14.0-STABLE (...) [00:20:45] Jail 14-0-S-amd64 14.0-STABLE amd64 is ready to be used root@poudriere-devel-14-stable:~ # poudriere jail -l JAILNAME VERSION ARCH METHOD TIMESTAMP PATH 14-0-S-amd64 14.0-STABLE amd64 http 2024-03-06 09:44:27 /usr/local/poudriere/jails/14-0-S-amd64 root@poudriere-devel-14-stable:~ # poudriere ports -c -p idm [00:00:00] Creating idm fs at /usr/local/poudriere/ports/idm... done [00:00:00] Cloning the ports tree... done root@poudriere-devel-14-stable:~ # poudriere ports -l PORTSTREE METHOD TIMESTAMP PATH idm git+https 2024-03-06 10:10:53 /usr/local/poudriere/ports/idm
Poudriere Server – Build FreeIPA/IDM Client Packages
Now we will choose needed options for our FreeBSD Ports and then start the bulk process of fetching and building them.
root@poudriere-devel-14-stable:~ # poudriere options -c -n -p idm security/cyrus-sasl2-gssapi // SELECT: (*) GSSAPI_MIT root@poudriere-devel-14-stable:~ # poudriere options -c -n -p idm net/openldap26-client // SELECT: [x] GSSAPI root@poudriere-devel-14-stable:~ # poudriere options -c -n -p idm security/sudo // DESELECT: [ ] PAM // SELECT: (*) GSSAPI_MIT // SELECT: (*) SSSD2 root@poudriere-devel-14-stable:~ # cat << EOF > /usr/local/etc/poudriere.d/idm security/krb5 security/sudo security/sssd2 security/cyrus-sasl2 security/cyrus-sasl2-gssapi security/pam_mkhomedir net/openldap26-client net/samba416 EOF root@poudriere-devel-14-stable:~ # poudriere bulk -j 14-0-S-amd64 -b latest -p idm -f /usr/local/etc/poudriere.d/idm root@poudriere-devel-14-stable:~ # zfs list NAME USED AVAIL REFER MOUNTPOINT zroot 1.51G 94.9G 24K none zroot/usr 1.39G 94.9G 24K none zroot/usr/local 1.39G 94.9G 24K none zroot/usr/local/poudriere 1.39G 94.9G 24K none zroot/usr/local/poudriere/jails 1.07G 94.9G 24K none zroot/usr/local/poudriere/jails/14-0-S-amd64 1.07G 94.9G 1.07G /usr/local/poudriere/jails/14-0-S-amd64 zroot/usr/local/poudriere/ports 328M 94.9G 24K none zroot/usr/local/poudriere/ports/idm 328M 94.9G 328M /usr/local/poudriere/ports/idm zroot/var 117M 94.9G 24K none zroot/var/ccache 117M 94.9G 117M /var/ccache
This is how the Poudriere build process looks like from the terminal … and a view for its new ZFS datasets that Poudriere created.
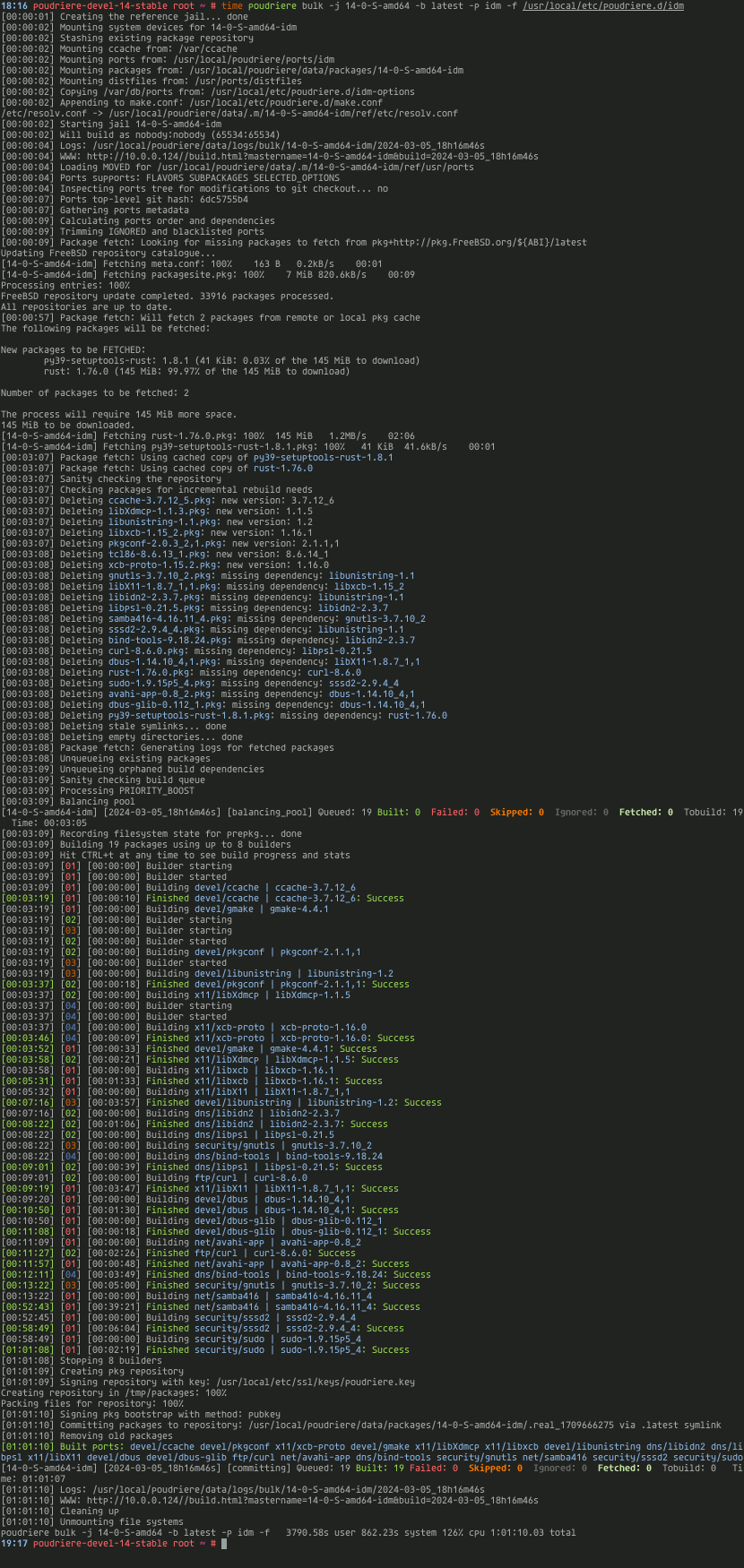
It was 2nd or 3rd run so when You first will run the bulk there will be more information about fetching packages etc.
Below You can see what processes are running in htop(1) during the build.
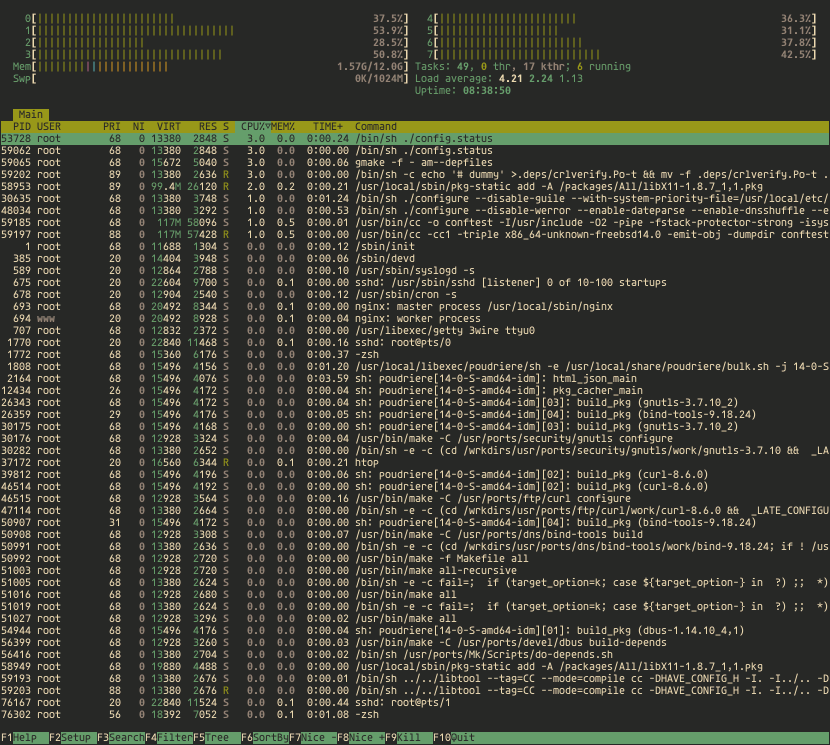
You can also follow the status of the build process in the browser at https://10.0.0.124 page.
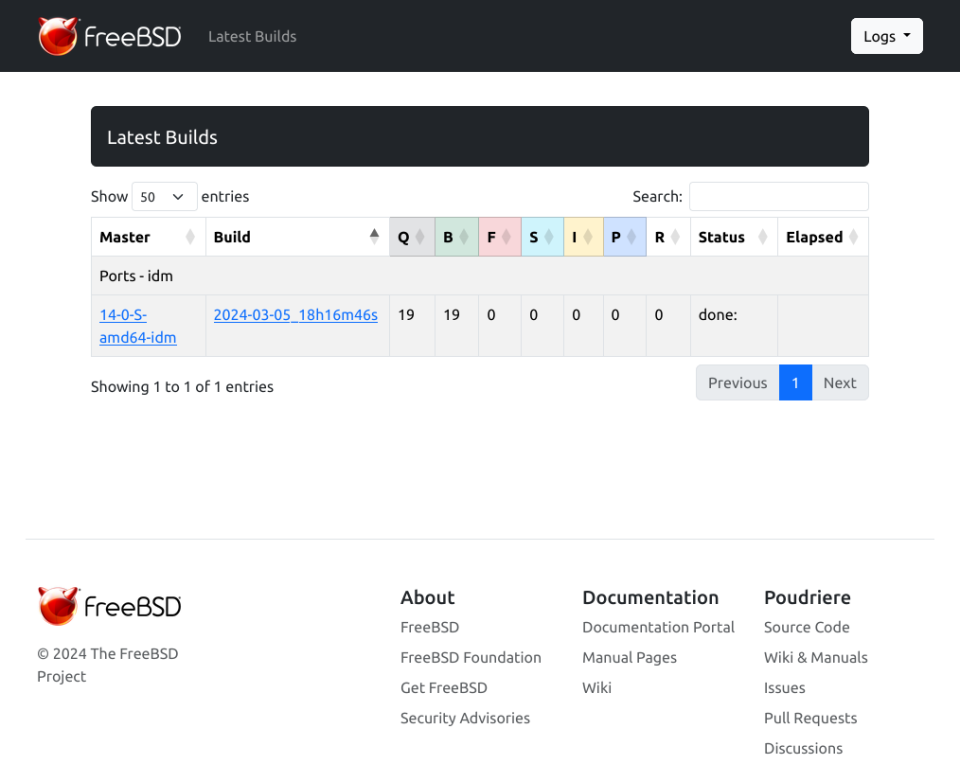
Generally the new Poudriere interface is quite ‘large’ I would say – so I use it at 70% scale/zoom on Firefox and IMHO its more usable like that.
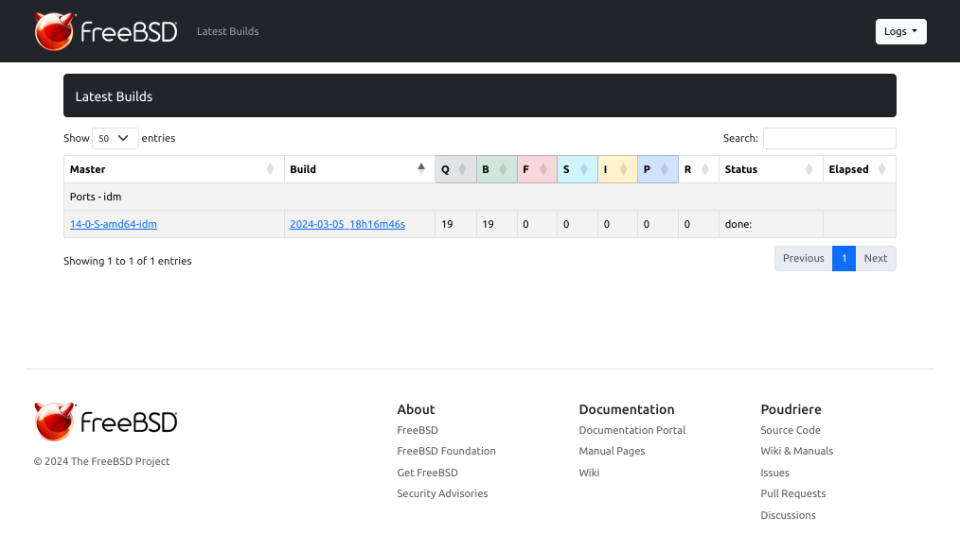
And below are the details about our build job.
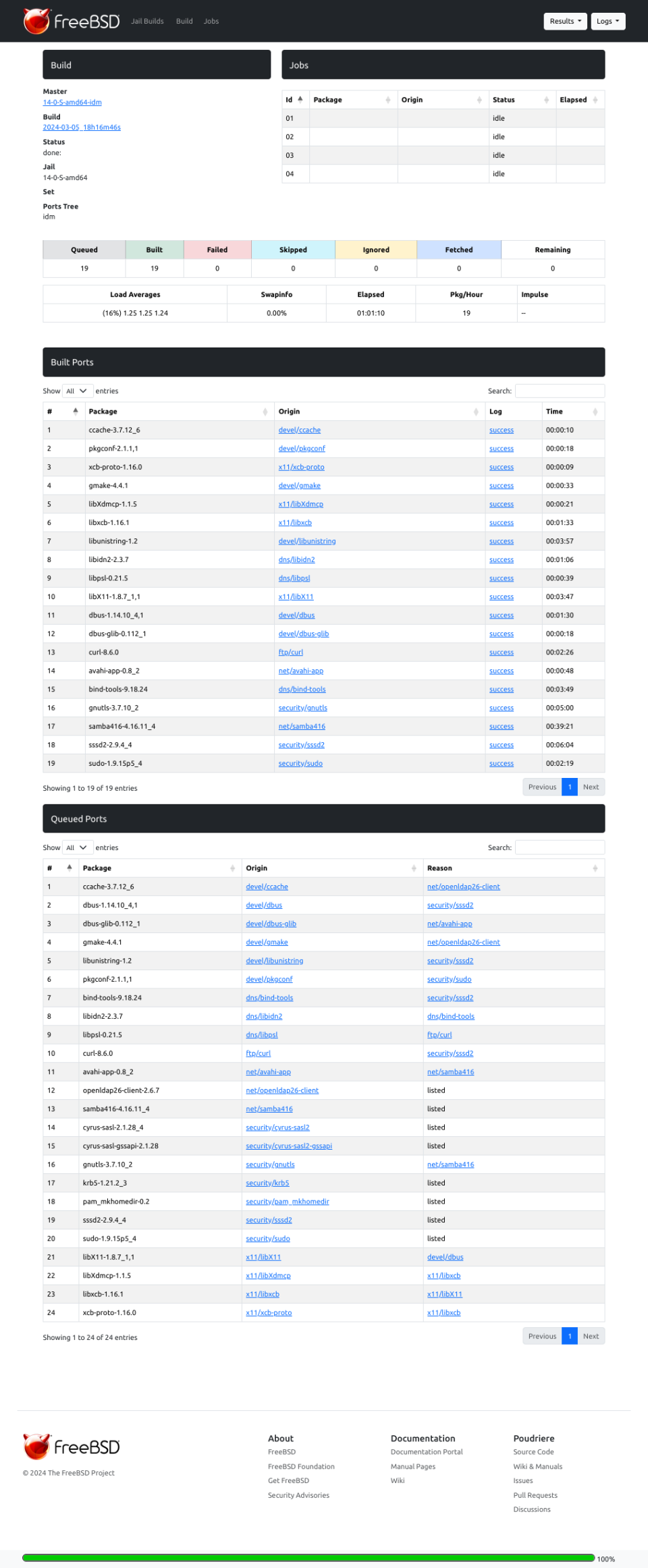
Poudriere Server – Update Repo/Packages
Everytime you will need to update the packages in that FreeIPA/IDM repo You will need to run these commands.
root@poudriere-devel-14-stable:~ # poudriere ports -u -p idm root@poudriere-devel-14-stable:~ # poudriere bulk -j 14-0-S-amd64 -b latest -p idm -f /usr/local/etc/poudriere.d/idm
You may as well update the FreeBSD Jail when needed.
root@poudriere-devel-14-stable:~ # poudriere jail -u -j 14-0-S-amd64
FreeBSD 14.0-STABLE Client – Setup
I will not repeat the process – but the same as with Poudriere server – you need to create FreeBSD client – for example as Bhyve VM.
Now – the needed configuration on FreeBSD 14.0-STABLE system to connect it to FreeIPA/IDM server.
root@idm-client:~ # :> ~/.hushlogin root@idm-client:~ # mkdir -p \ /usr/local/etc/ipa \ /var/log/sssd \ /var/run/sss/private \ /var/db/sss root@idm-client:~ # echo '10.0.0.233 idm-client.lab.org idm-client' >> /etc/hosts root@idm-client:~ # echo '10.0.0.200 idm.lab.org idm' >> /etc/hosts root@idm-client:~ # hostname idm-client.lab.org root@idm-client:~ # sysrc hostname=idm-client.lab.org root@idm-client:~ # fetch -o /usr/local/etc/ipa/ca.crt http://idm.lab.org/ipa/config/ca.crt
Now we will need to add or FreeBSD client to FreeIPA/IDM. Instructions below.
[root@idm ~]# kinit admin [root@idm ~]# ipa dnsrecord-add lab.org idm-client --a-rec=10.0.0.233 --a-create-reverse Record name: idm-client A record: 10.0.0.233 [root@idm ~]# ipa host-add idm-client.lab.org ------------------------------- Added host "idm-client.lab.org" ------------------------------- Host name: idm-client.lab.org Principal name: host/idm-client.lab.org@LAB.ORG Principal alias: host/idm-client.lab.org@LAB.ORG Password: False Keytab: False Managed by: idm-client.lab.org [root@idm ~]# ipa-getkeytab -s idm.lab.org -p host/idm-client.lab.org@LAB.ORG -k /root/idm-client.lab.org.keytab Keytab successfully retrieved and stored in: /root/idm-client.lab.org.keytab [root@idm ~]# cp /root/idm-client.lab.org.keytab /usr/share/ipa/html/ [root@idm ~]# chmod 644 /usr/share/ipa/html/idm-client.lab.org.keytab
Now lets get back to our FreeBSD client.
root@idm-client:~ # fetch -o /usr/local/etc/ipa/krb5.keytab \ http://idm.lab.org/ipa/config/idm-client.lab.org.keytab root@idm-client:~ # chmod 600 /usr/local/etc/ipa/krb5.keytab root@idm-client:~ # mkdir -p /usr/local/etc/ssl/certs root@idm-client:~ # mkdir -p /usr/local/etc/pkg/repos root@idm-client:~ # sed -e 's|quarterly|latest|g' /etc/pkg/FreeBSD.conf \ > /usr/local/etc/pkg/repos/FreeBSD.conf root@idm-client:~ # pkg install -y beadm root@idm-client:~ # fetch -o /usr/local/etc/ssl/certs/poudriere.cert \ http://poudriere-devel-14-stable.lab.org/data/poudriere.cert root@idm-client:~ # export IP=10.0.0.124 root@idm-client:~ # cat << EOF > /usr/local/etc/pkg/repos/14-0-S-amd64.conf 14-0-S-amd64-idm: { url: "http://${IP}/packages/14-0-S-amd64-idm/", mirror_type: "http", signature_type: "pubkey", pubkey: "/usr/local/etc/ssl/certs/poudriere.cert", enabled: yes, priority: 100 } EOF root@idm-client:~ # pkg update -f root@idm-client:~ # pkg install -y \ krb5 \ sudo \ sssd2 \ cyrus-sasl \ cyrus-sasl-gssapi \ openldap26-client \ pam_mkhomedir root@idm-client:~ # cat << EOF >> /etc/ssh/ssh_config GSSAPIAuthentication yes EOF root@idm-client:~ # cat << EOF >> /etc/ssh/sshd_config GSSAPIAuthentication yes UsePAM yes EOF root@idm-client:~ # cat << EOF > /usr/local/etc/sssd/sssd.conf [sssd] config_file_version = 2 services = pam, ssh, sudo, ifp, pac, nss domains = lab.org timeout = 20 [domain/lab.org] ipa_server = idm.lab.org ipa_domain = lab.org pam_gssapi_services = sudo, sudo-i enumerate = True cache_credentials = True override_shell = /usr/local/bin/bash override_homedir = /home/%u default_shell = /bin/sh ldap_group_nesting_level = 10 default_ccache_template = FILE:/tmp/krb5cc_:%U krb5_ccache_template = FILE:/tmp/krb5cc_:%U krb5_server = idm.lab.org:88 krb5_realm = LAB.ORG krb5_keytab = /usr/local/etc/ipa/krb5.keytab krb5_auth_timeout = 20 id_provider = ipa sudo_provider = ipa access_provider = ipa subdomains_provider = ipa auth_provider = ipa chpass_provider = ipa selinux_provider = none EOF root@idm-client:~ # chmod 600 /usr/local/etc/sssd/sssd.conf root@idm-client:~ # cat << EOF > /etc/nsswitch.conf # # nsswitch.conf(5) - name service switch configuration file # $FreeBSD$ # group: files sss group_compat: nis hosts: files dns networks: files passwd: files sss passwd_compat: nis shells: files services: compat services_compat: nis protocols: files rpc: files sudoers: sss files netgroup: files EOF root@idm-client:~ # cat /etc/rc.conf hostname="idm-client.lab.org" ifconfig_vtnet0="inet 10.0.0.233/24" defaultrouter="10.0.0.1" syslogd_flags="-ss" clear_tmp_enable="YES" sshd_enable="YES" zfs_enable="YES" sssd_enable="YES" root@idm-client:~ # cat << EOF > /usr/local/etc/openldap/ldap.conf BASE dc=org,dc=lab URI ldap://idm.lab.org/ SASL_MECH GSSAPI SASL_REALM LAB.ORG ssl start_tls TLS_CACERT /usr/local/etc/ipa/ca.crt EOF root@idm-client:~ # cat << EOF > /etc/krb5.conf [libdefaults] default_realm = LAB.ORG default_keytab_name = FILE:/usr/local/etc/ipa/krb5.keytab default_tkt_enctypes = aes256-cts des-cbc-crc aes128-cts arcfour-hmac default_tgs_enctypes = aes256-cts des-cbc-crc aes128-cts arcfour-hmac dns_lookup_realm = false dns_lookup_kdc = false rdns = false ticket_lifetime = 24h forwardable = yes [realms] LAB.ORG = { kdc = idm.lab.org:88 master_kdc = idm.lab.org:88 admin_server = idm.lab.org:749 default_domain = lab.org pkinit_anchors = FILE:/usr/local/etc/ipa/ca.crt } [domain_realm] .lab.org = LAB.ORG lab.org = LAB.ORG [logging] kdc = FILE:/var/log/krb5/krb5kdc.log admin_server = FILE:/var/log/krb5/kadmin.log kadmin_local = FILE:/var/log/krb5/kadmin_local.log default = FILE:/var/log/krb5/krb5lib.log EOF root@idm-client:~ # cat << EOF > /etc/pam.d/system # # # System-wide defaults # # AUTH auth sufficient pam_krb5.so no_warn try_first_pass # auth sufficient pam_ssh.so no_warn try_first_pass auth sufficient /usr/local/lib/pam_sss.so no_warn use_first_pass auth required pam_unix.so no_warn try_first_pass nullok # ACCOUNT # account required pam_krb5.so account required pam_login_access.so account required /usr/local/lib/pam_sss.so ignore_unknown_user ignore_authinfo_unavail account required pam_unix.so # SESSION # session optional pam_ssh.so want_agent session required pam_lastlog.so no_fail session required /usr/local/lib/pam_mkhomedir.so mode=0700 # PASSWORD # password sufficient pam_krb5.so no_warn try_first_pass password sufficient /usr/local/lib/pam_sss.so no_warn use_authtok password required pam_unix.so no_warn try_first_pass EOF root@idm-client:~ # cat << EOF > /etc/pam.d/sshd # # # PAM configuration for the "sshd" service # # AUTH auth sufficient pam_krb5.so no_warn try_first_pass # auth sufficient pam_ssh.so no_warn try_first_pass auth sufficient /usr/local/lib/pam_sss.so no_warn use_first_pass auth required pam_unix.so no_warn try_first_pass # ACCOUNT account required pam_nologin.so # account required pam_krb5.so account required pam_login_access.so account required pam_unix.so account required /usr/local/lib/pam_sss.so ignore_unknown_user ignore_authinfo_unavail # SESSION # session optional pam_ssh.so want_agent session required pam_permit.so session required /usr/local/lib/pam_mkhomedir.so mode=0700 session optional /usr/local/lib/pam_sss.so # PASSWORD # password sufficient pam_krb5.so no_warn try_first_pass password sufficient /usr/local/lib/pam_sss.so no_warn use_authtok password required pam_unix.so no_warn try_first_pass EOF
Our idm-client.lab.org in the FreeIPA/IDM below.
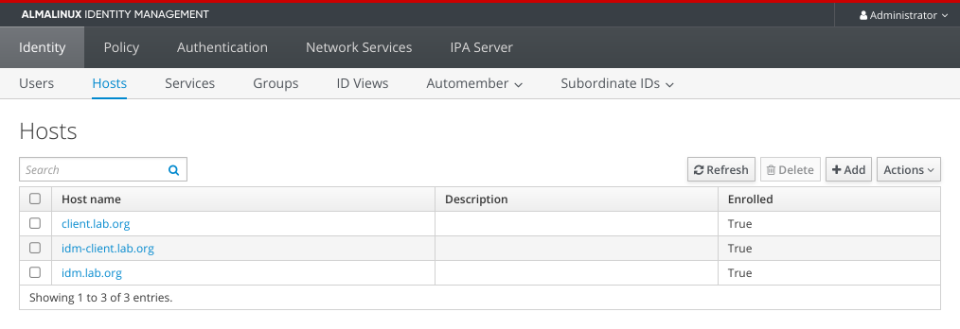
Now reboot your idm-client.lab.org and You should be able to login to it with FreeIPA/IDM account.
host # ssh vermaden@10.0.0.233 (vermaden@10.0.0.233) Password: Last login: Wed Mar 6 07:04:42 2024 vermaden@idm-client:~ $ id uid=1374600003(vermaden) gid=1374600000(admins) groups=1374600000(admins) vermaden@idm-client:~ $ klist Credentials cache: FILE:/tmp/krb5cc_1374600003 Principal: vermaden@LAB.ORG Issued Expires Principal Mar 6 07:04:34 2024 Mar 7 06:19:19 2024 krbtgt/LAB.ORG@LAB.ORG vermaden@idm-client:~ $ sudo -i Password for vermaden@LAB.ORG: root@idm-client:~ # id uid=0(root) gid=0(wheel) groups=0(wheel),5(operator)
FreeBSD 14.0-STABLE Client – Debug Commands
Below are some commands that you may (or may not) find useful.
root@idm-client:~ # sssctl user-checks vermaden user: vermaden action: acct service: system-auth SSSD nss user lookup result: - user name: vermaden - user id: 1374600003 - group id: 1374600000 - gecos: Vermaden Nedamrev - home directory: /home/vermaden - shell: /bin/sh Unable to connect to system bus! InfoPipe User lookup with [vermaden] failed. testing pam_acct_mgmt pam_acct_mgmt: Success PAM Environment: - no env - root@idm-client:~ # ldapsearch -H ldap://idm.lab.org -x -b "" -s base -LLL supportedSASLMechanisms dn: supportedSASLMechanisms: EXTERNAL supportedSASLMechanisms: GSS-SPNEGO supportedSASLMechanisms: GSSAPI supportedSASLMechanisms: DIGEST-MD5 supportedSASLMechanisms: CRAM-MD5 supportedSASLMechanisms: LOGIN supportedSASLMechanisms: PLAIN supportedSASLMechanisms: ANONYMOUS root@idm-client:~ # ldapsearch -x -v -W -D 'cn=Directory Manager' uid=vermaden ldap_initialize( ) Enter LDAP Password: filter: uid=vermaden requesting: All userApplication attributes # extended LDIF # # LDAPv3 # base (default) with scope subtree # filter: uid=vermaden # requesting: ALL # # search result search: 2 result: 32 No such object # numResponses: 1 root@idm-client:~ # ldapsearch -Y GSSAPI -Omaxssf=0 -H ldaps://idm.lab.org -b dc=lab,dc=org CN=vermaden SASL/GSSAPI authentication started SASL username: vermaden@LAB.ORG SASL SSF: 0 # extended LDIF # # LDAPv3 # base with scope subtree # filter: CN=vermaden # requesting: ALL # # vermaden, groups, compat, lab.org dn: cn=vermaden,cn=groups,cn=compat,dc=lab,dc=org objectClass: posixGroup objectClass: ipaOverrideTarget objectClass: ipaexternalgroup objectClass: top gidNumber: 1374600003 ipaAnchorUUID:: OklQQTpsYWIub3JnOjcyN2FlMjM2LTMyMTktMTFlZS04OGMyLTU4OWNmYzA4MW QzNQ== cn: vermaden # vermaden, groups, accounts, lab.org dn: cn=vermaden,cn=groups,cn=accounts,dc=lab,dc=org objectClass: posixgroup objectClass: ipaobject objectClass: mepManagedEntry objectClass: top cn: vermaden gidNumber: 1374600003 description: User private group for vermaden mepManagedBy: uid=vermaden,cn=users,cn=accounts,dc=lab,dc=org ipaUniqueID: 727ae236-3219-11ee-88c2-589cfc081d35 # search result search: 4 result: 0 Success # numResponses: 3 # numEntries: 2
Thats it – you have FreeBSD 14.0-STABLE connected to FreeIPA/IDM server.
Summary
Let me know in comments how it went.
Should
“that security/sssd is not deprecated”
be
“that security/sssd is NOW deprecated” ?
LikeLike
Thank You. Fixed 🙂
LikeLike
I’m also getting the error:
When running sssctl user-checks $user
I tried enabling D-Bus but then it just timeouts instead, did you experiment with this?
LikeLike
I did not investigated that as I assumed it is some small Linuxism – fortunately IMHO harmless as you can login and use sudo(8) with IDM credentials.
LikeLike
Pingback: Keycloak Identity and Access Management on FreeBSD | 𝚟𝚎𝚛𝚖𝚊𝚍𝚎𝚗
Pingback: Valuable News – 2024/03/11 | 𝚟𝚎𝚛𝚖𝚊𝚍𝚎𝚗
I think
root@idm-client:~ # fetch -o /usr/local/etc/ssl/certs/poudriere.cert http://idm.lab.org/data/poudriere.cert
should be
root@idm-client:~ # fetch -o /usr/local/etc/ssl/certs/poudriere.cert http://poudriere-devel-14-stable.lab.org/data/poudriere.cert
🙂
LikeLiked by 1 person
You are right.
Gonna fix that now 🙂
LikeLike